- Published on
What is DDoS (Distributed Denial of Service)?
DDoS stands for Distributed Denial of Service.
It’s a type of cyberattack where many machines attack a target at the same time, overwhelming it so legitimate users can’t access the service.
What happens in a DDoS attack?
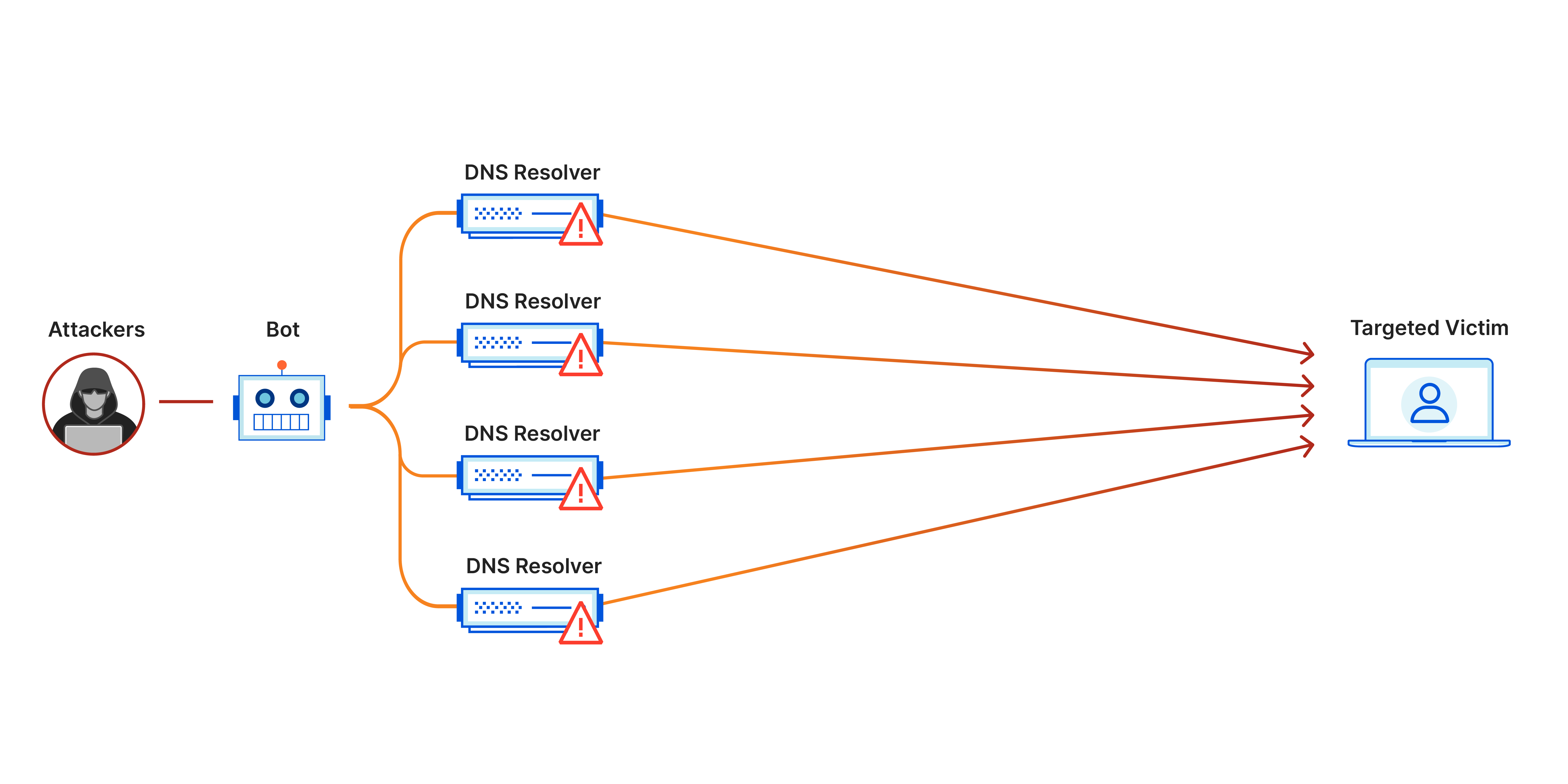
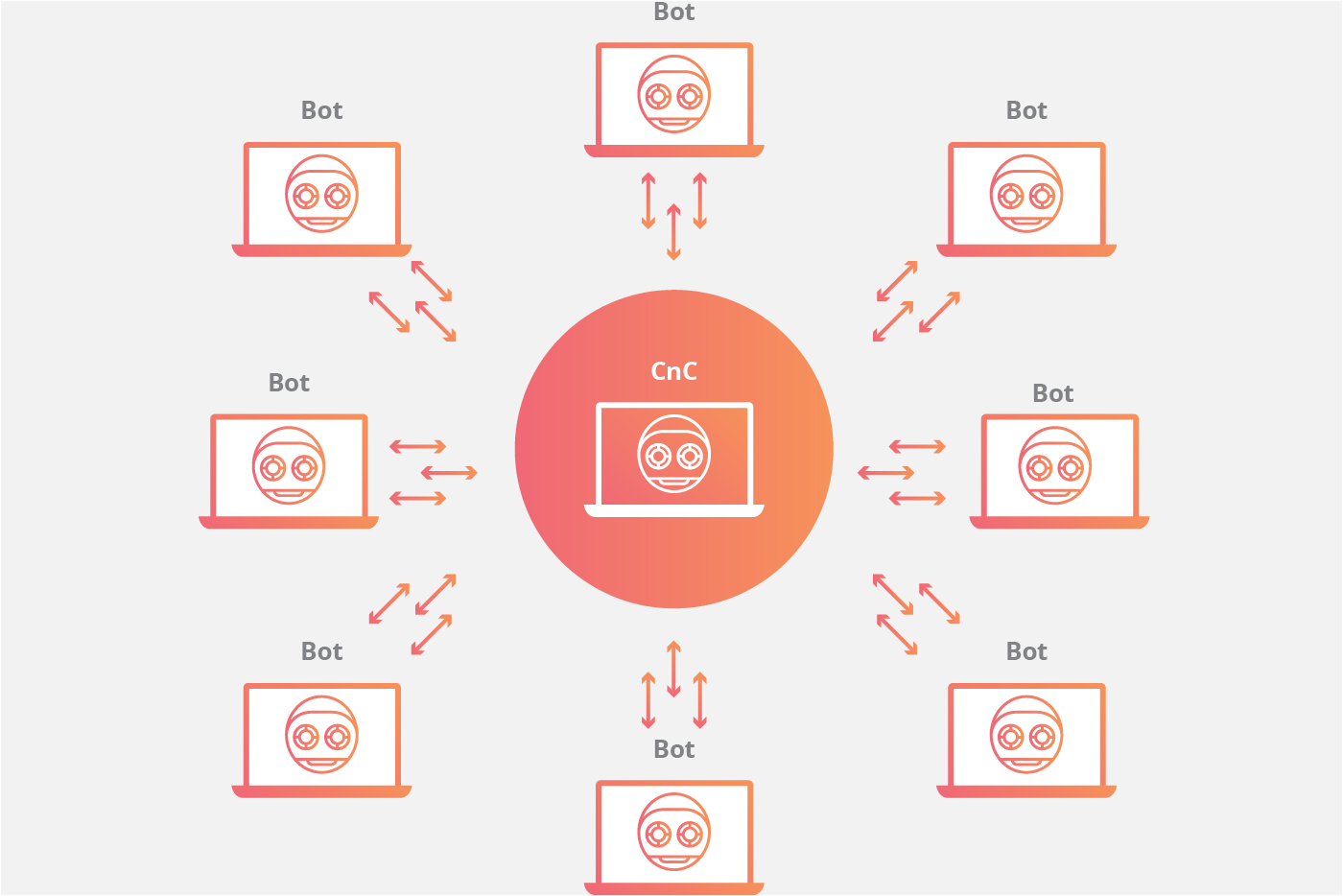


Attacker controls many devices These devices are often compromised computers, servers, or IoT devices (called a botnet).
All devices send traffic simultaneously They flood the target (website, API, game server, etc.) with requests.
Target is overwhelmed
- CPU maxed out
- Memory exhausted
- Network bandwidth saturated
Legitimate users are denied service The site becomes slow or completely unavailable.
Why is it called Distributed?
Because the attack doesn’t come from one place — it comes from thousands or millions of sources across the internet, making it very hard to block.
Common types of DDoS attacks
1. Volume-based attacks
- Goal: Consume bandwidth
- Example: UDP flood, ICMP (ping) flood
- Think: “Too much traffic on the highway”
2. Protocol attacks
- Goal: Exhaust server resources
- Example: SYN flood
- Exploits weaknesses in network protocols
3. Application-layer attacks
- Goal: Crash specific services
- Example: HTTP GET/POST flood
- Looks like normal user traffic → hardest to detect
Simple analogy
Imagine a restaurant:
- Normal customers: manageable
- Suddenly 10,000 fake customers walk in and order nothing
- Real customers can’t get a seat ➡️ That’s DDoS
What DDoS is not
- ❌ Not hacking into your system
- ❌ Not stealing data
- ✅ It’s about making your service unavailable
How organizations defend against DDoS
- Rate limiting
- Traffic filtering
- Load balancers
- CDNs (e.g. Cloud-based DDoS protection)
- Anycast routing
One-sentence summary
A DDoS attack overwhelms a service with massive, distributed traffic so real users can’t access it.